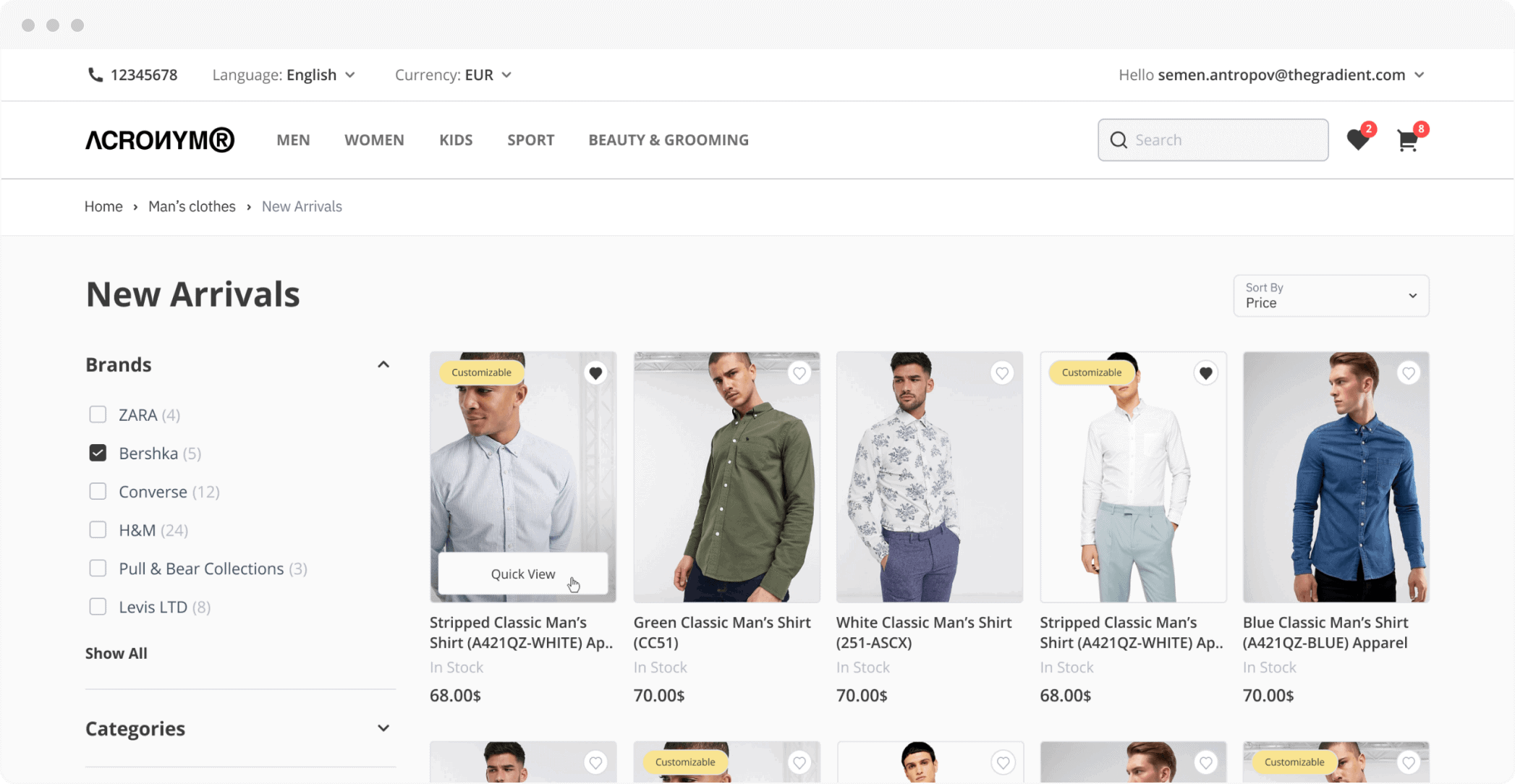
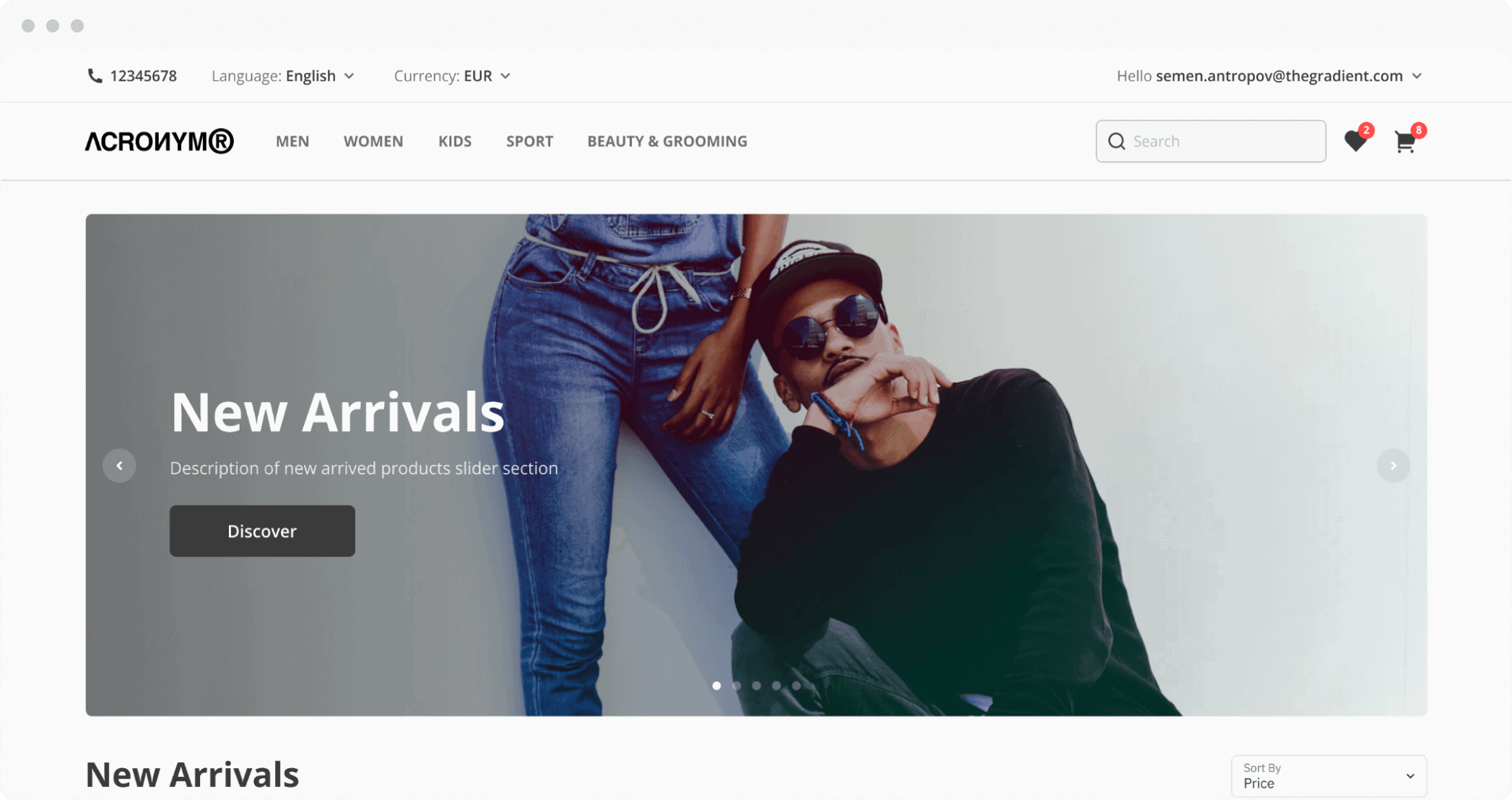
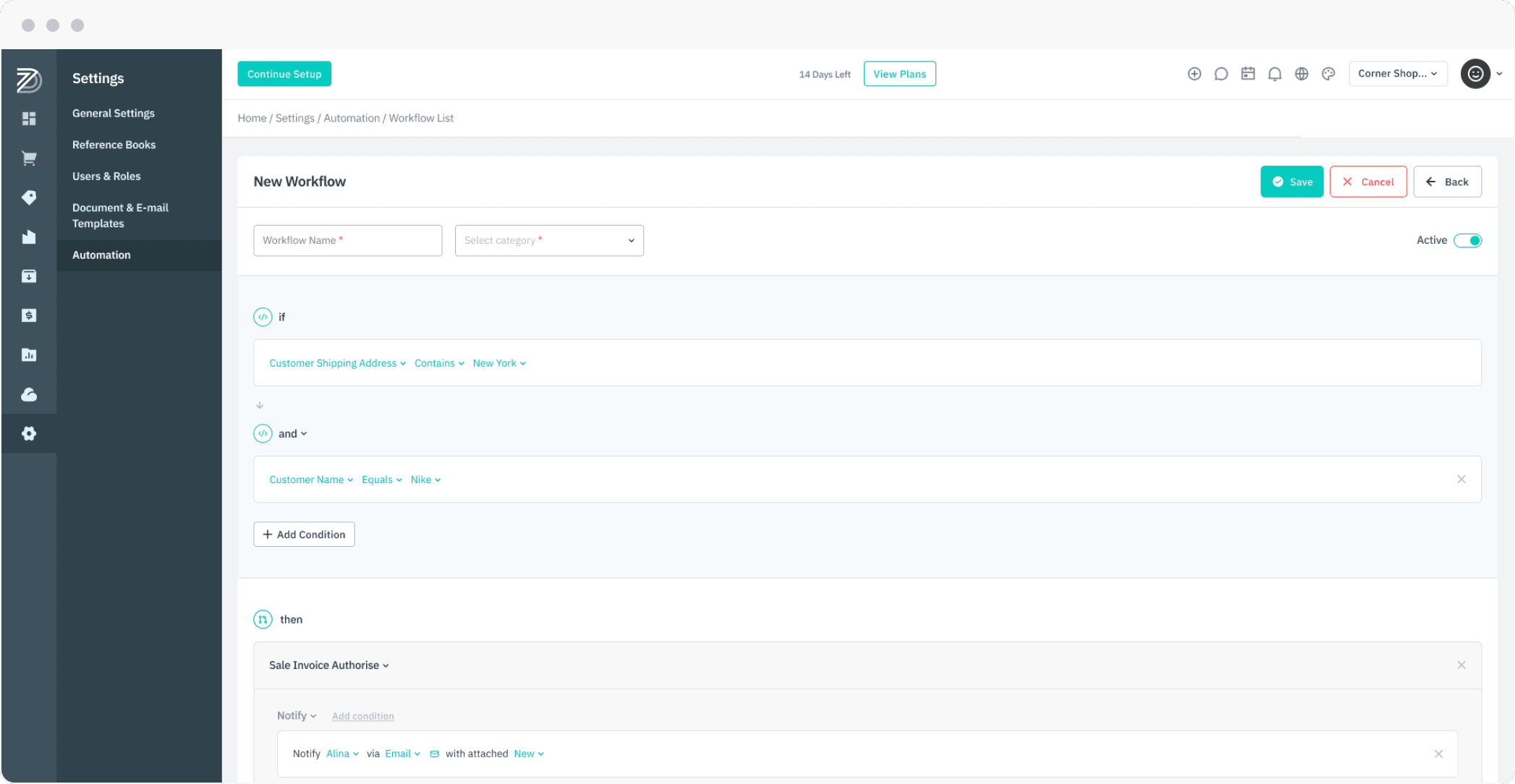
Inventory Management
With Cin7 Core Inventory, you’ll be equipped with instant visibility into stock levels and order status, for up-to the-minute knowledge of your inventory. And because you need to focus on growing your business, you can rely on robust automated processes to save you time and keep your stock right where it need to be.
B2B Portal
Invite retail and wholesale customers to join your own branded B2B Portal.
Point of Sale
Cin7 Core POS can be used on iPad, Android, PC & Mac, giving you complete freedom of choice in devices.
E-commerce & Marketplace
Download products from ecommerce store to Cin7 Core. All stock level changes will be automatically pushed to ecommerce store.
Phone & Email Notification
Get instant notifications about changing stock levels and your store’s product inventory. We always keep you in the loop.
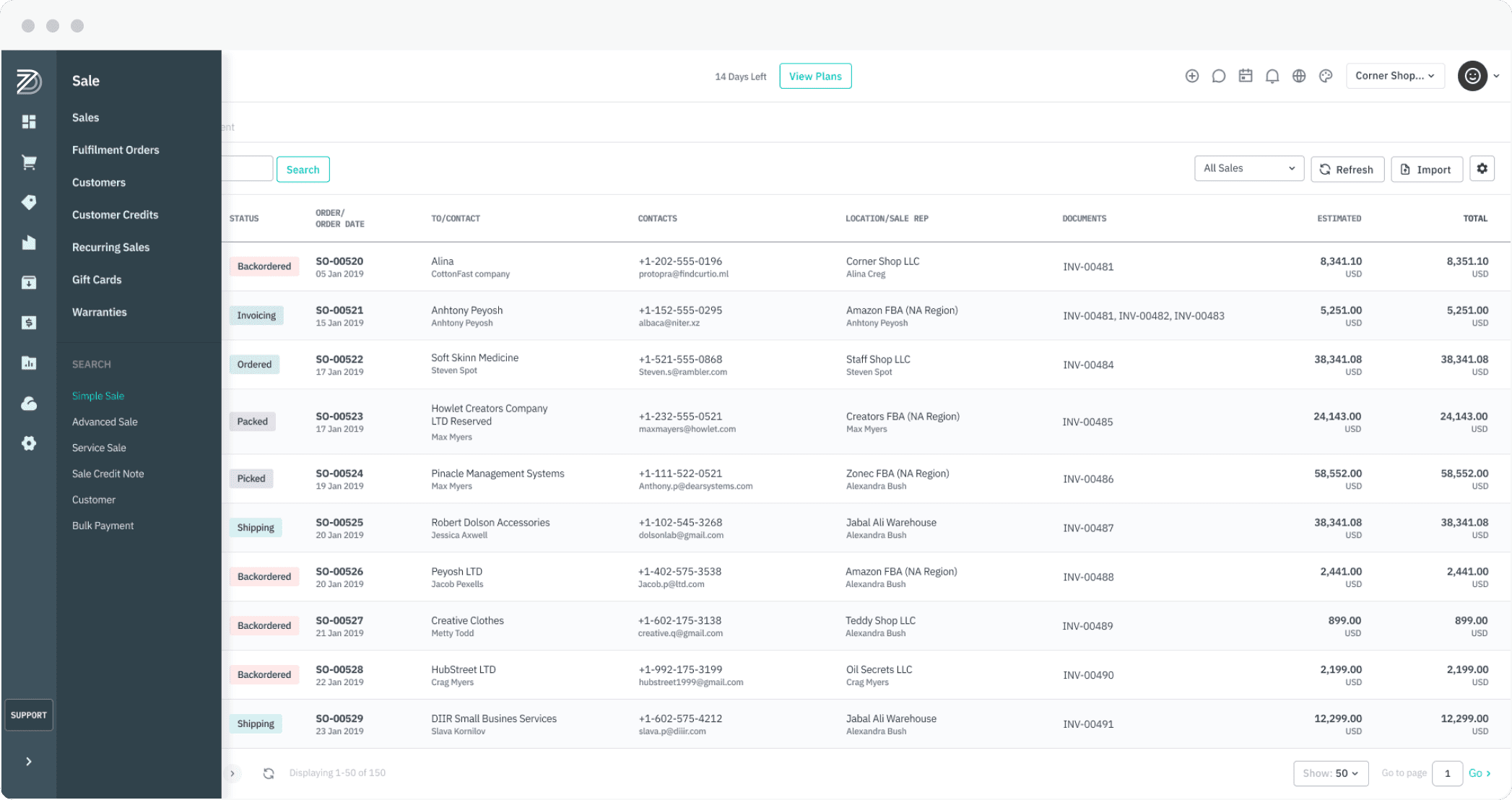
Purchase Orders
Update the quantities of your products in real time and sync them seamlessly across all stores and devices. This gives you complete control of your inventory.
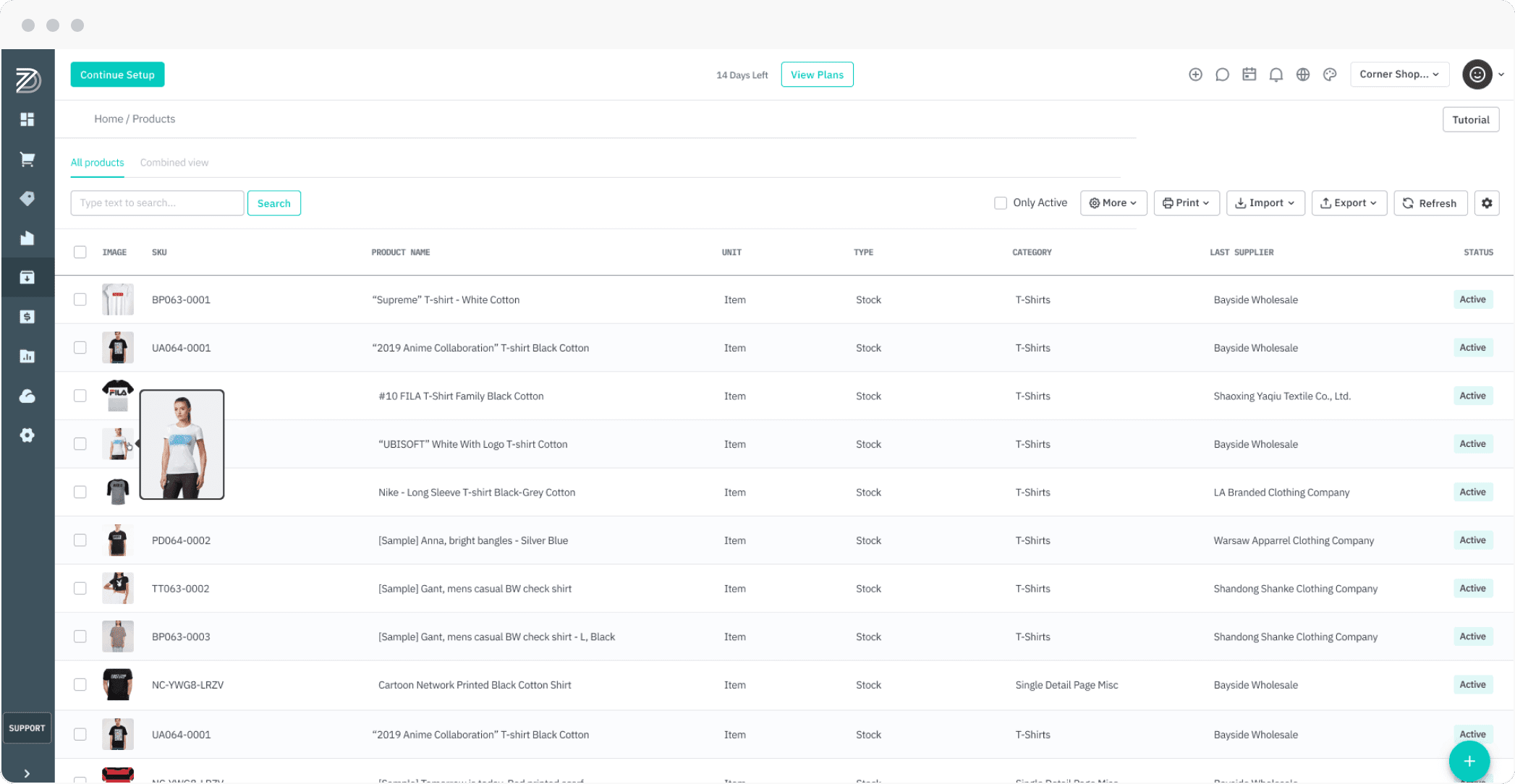
Inventory Quantities
Update the quantities of your products in real time and sync them seamlessly across all stores and devices. This gives you complete control of your inventory.
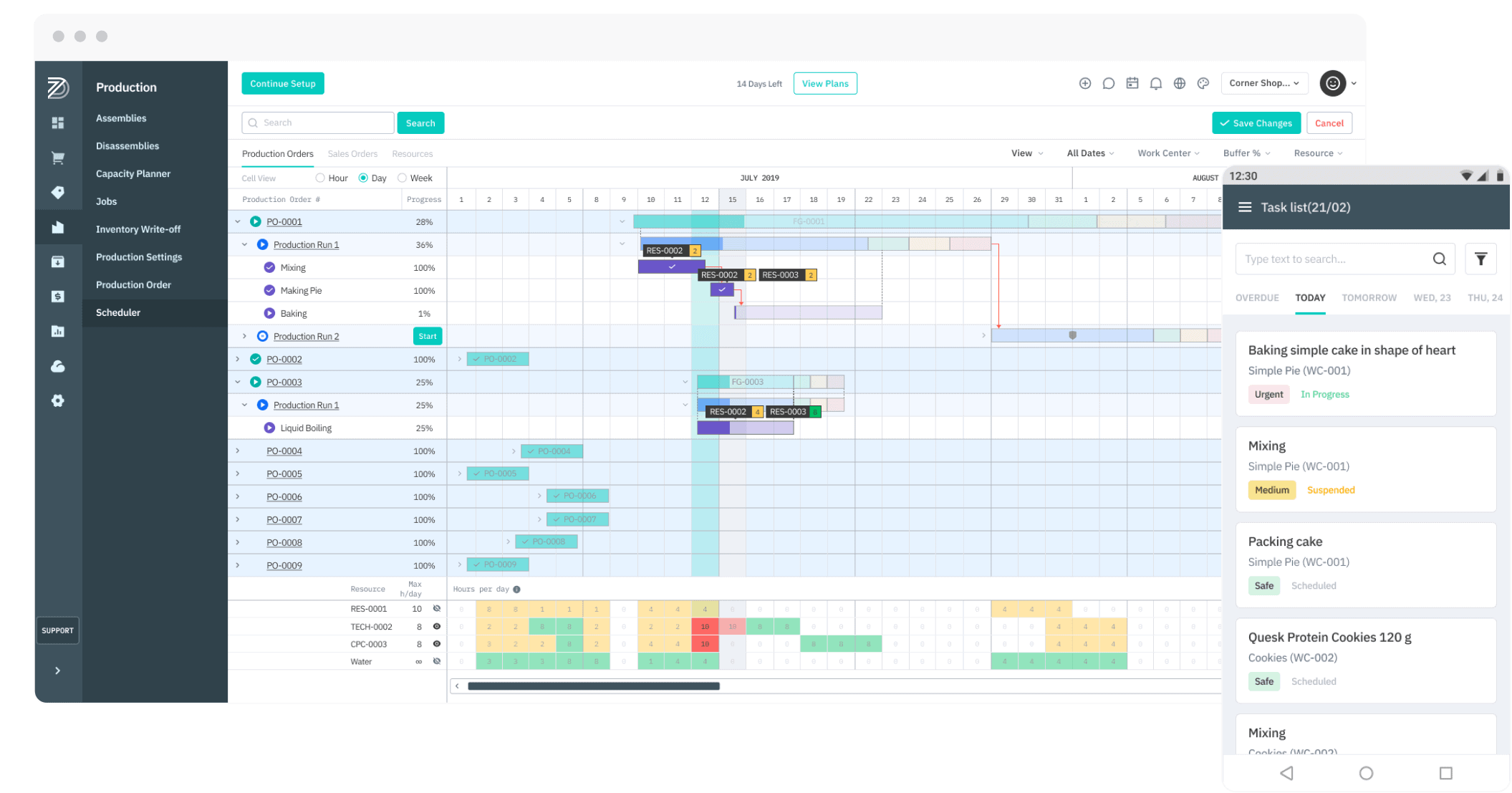
Manufacturing
With Cin7 Core, creating a detailed Bill of Materials for your inventory and subassemblies is simple, giving you a true picture of raw material, labour and overhead costs.
Supplies
By recording your entire purchase history, Cin7 Core allows you to access comprehensive supplier information, powering intelligent decision-making and minimizing financial losses.
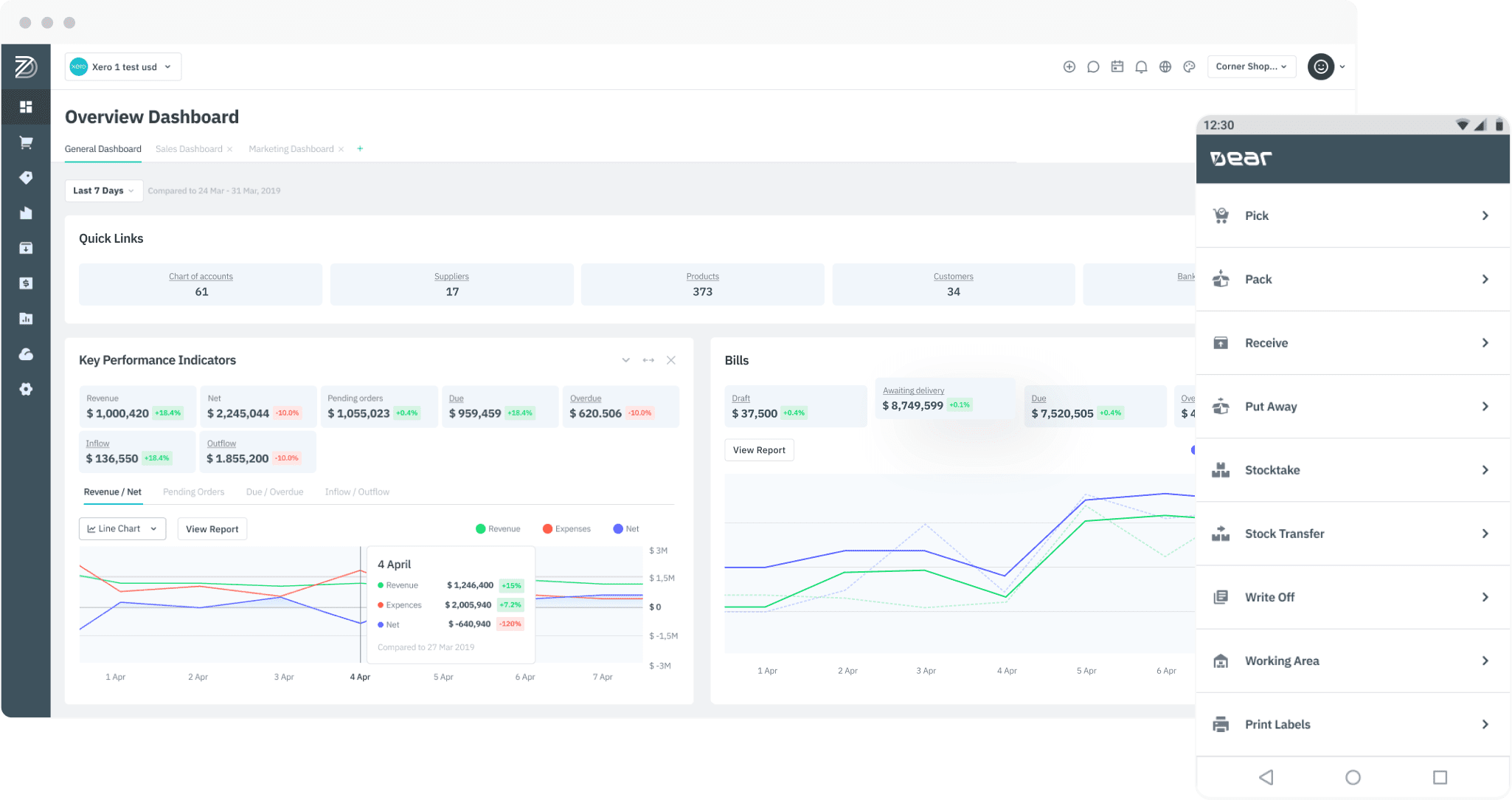
Accounting
Imagine the time and labour you could save if every accounting process was beautifully streamlined and perfectly integrated across your business. Cin7 Core does exactly that.
Customers
Our powerful platform helps you save your customers information including multiple contact details and purchase histories.

 Back to Top
Back to Top